The Kids In Touch app is powered by a MongoDB database. My db is hosted by ObjectRocket. ObjectRocket has some great features for scaling dbs. It is designed to be able to shard on the fly. It's also got some great security features like Access Control Lists (ACL). With the ACL's, you can prevent access to the database from any unauthorized IP address. This is a great way of ensuring that only your application servers can access the db.
When I'm working from home (95% of the time), I can access my ObjectRocket instance easily because my home IP address is in the ACL. Unfortunately, when I'm away from the house, things get a little tougher. I don't have a consistent IP address to add to the ACL.
To overcome this, I've been logging into one of my servers and then accessing the db from that command line. This is okay when I'm doing command line style work. However, it's impossible if I want to use a GUI like JSON Studio or RoboMongo. For the last few months, I just haven't bothered solving this problem. However, this entire week, I've been out of the office. I needed to deal with this issue.
SSH Port Forwarding to the Rescue! : SSH Port forwarding allows your local machine to access a remote server (Server Z) THROUGH another server you control (Server A). Server Z simply thinks that Server A is connecting to it - because that's exactly what's happening. However, your Server A is redirecting your traffic to Server Z.
A simple example:
ssh -L8080:www.google.com:80 [email protected]
This would allow you to access Google on your local port 8080 as if you were coming from your remote server. As far as Google knows, you are the server at the XXX.XXX.XXX.XXX IP address. Privacy FTW!
So, how do you know this really works? The proof is in the pudding! Here's another example:
ssh -L8080:www.whatismyip.com:80 [email protected]
Semi-Obnoxious Ad : If you need a messaging app for your young kids, please consider Kids in Touch
This is connecting your localhost port 8080 to an IP Address Detection Service. Once you have the SSH tunnel up, in your browser, open the address http://localhost:8080. Since WhatIsMyIP uses cloudflare, you'll not really get what you wanted. Instead, you'll get a security warning. However, hiding in that security warning is your server's IP address. That proves that your Port 8080 traffic is being tunneled through your server.
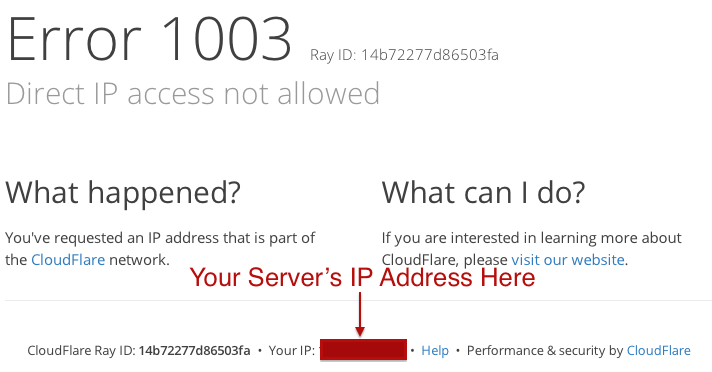
Now, let's see how this works with ObjectRocket. First, to connect to an ObjectRocket instance, you need their connection string. It looks something like :
iad-mongos0.objectrocket.com:1XXXX
or
iad-mongos0.objectrocket.com:2XXXX
The sample with a port of 1XXXX is the non-SSL connection. The 2XXXX is the SSL connection.
So, we need to appear to ObjectRocket as if we're a server in the ACL. This is accomplished with port forwarding just as above.
ssh -L2XXXX:iad-mongos0.objectrocket.com:2XXXX [email protected]
So now, in another terminal window, you can connect from your local machine to the ObjectRocket DB instance like this:
mongo localhost:2XXXX/db-name-goes-here
In your GUI, you create a new connection using the local port info.
Tada! You can now connect to any ACL controller ObjectRocket instance from any location where you're working