Do you believe online privacy is a right?
Do you go to great lengths to protect your own privacy?
Did you know Google has modified Chrome/Chromium to track users across the web directly in the browser?
If so, I strongly urge you and other developers take steps to protect the privacy of your customers and website visitors.
This "Federated Learning of Cohorts or FLoC" functionality cannot be disabled by browser users and automatically enlists your website into spying on visitors.
Even worse, since FLoC is enabled by default in Chromium, other browser vendors that use Chromium will automatically be spying as well unless they take steps to disable FLoC.
Fortunately, some browser vendors like Vivaldi have taken a strong stance on this issue.
If you believe in privacy, please protect your website visitors by disabling FLoC using HTTP headers (see "If you are a website owner").
If you use the self-hosted version of the excellent Ghost Blog, you'll have to tinker around at the command line to add the required FLoC opt-out headers. Follow these steps to configure Nginx.
IMPORTANT: Before making these changes, be sure to backup your original files!
sudo -i -u ghost-mgr
cd /etc/nginx/sites-available
vi your_domain_name.com-ssl.confNow, add this line to the location / section:
add_header Permissions-Policy interest-cohort=();In the end, the your_domain_name.com-ssl.conf file should look something like this:
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name your_domain_name.com;
root /var/www/ghost/system/nginx-root; # Used for acme.sh SSL verification (https://acme.sh)
ssl_certificate /etc/letsencrypt/your_domain_name.com/fullchain.cer;
ssl_certificate_key /etc/letsencrypt/your_domain_name.com/your_domain_name.com.key;
include /etc/nginx/snippets/ssl-params.conf;
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
add_header Permissions-Policy interest-cohort=();
proxy_pass http://127.0.0.1:2368;
}
location ~ /.well-known {
allow all;
}
client_max_body_size 50m;
}NOTE: If your site does not automatically redirect users to the HTTPS version of your URL, then you may need to make the same changes in the your_domain_name.com.conf file as well.
Finally, for these changes to take effect, you'll need to restart the Nginx server. You can do this with the following command at the terminal:
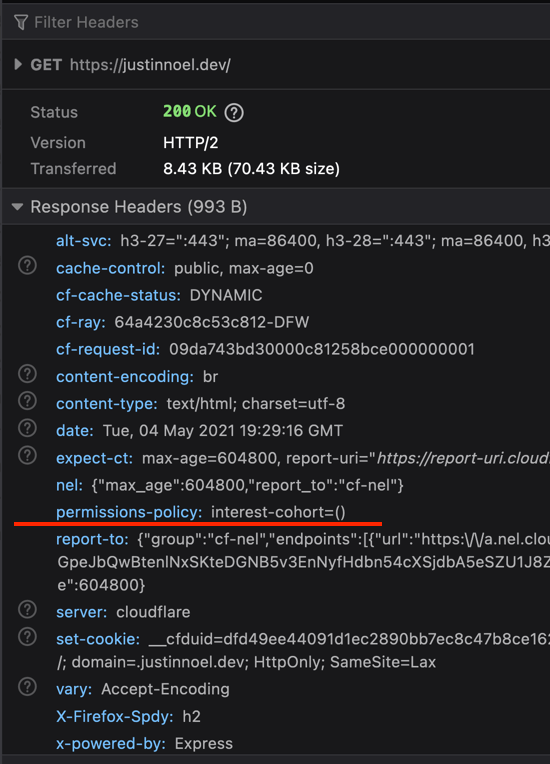
sudo systemctl restartNext, make sure your changes have taken effect by reloading one of your blog posts in a browser and inspecting the headers.
You should see something like this:
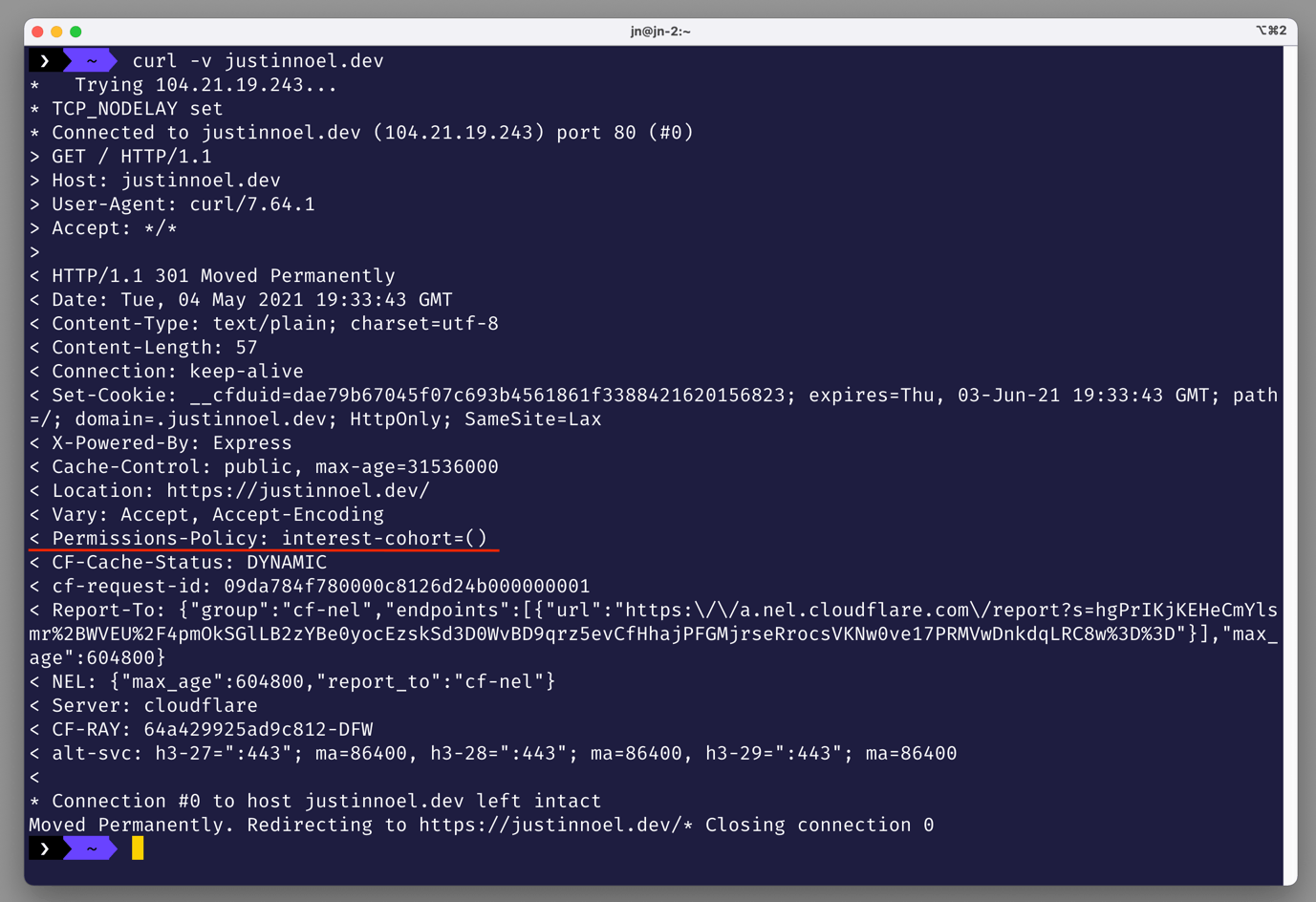
You can also use the curl -v command to see the results: